What's on this page?
Jump to:
- How Social Engineering Attacks Actually Work
- Common Types of Social Engineering Attacks
- Why Social Engineering Is So Hard to Defend Against
- How Organisations and Individuals Reduce the Risk
- Why Understanding Social Engineering Matters for a Cyber Career
- Key Takeaways: Explaining Social Engineering Simply
- Social Engineering FAQs
How Social Engineering Attacks Actually Work
At the centre of every social engineering attack is psychology. I always explain it as attackers understanding people better than they understand technology. They know how we think under pressure, how we respond to authority, and how easy it is to act quickly without stopping to question what’s really going on.
Instead of trying to break through firewalls or encryption, attackers target people, because people are unpredictable.
Systems behave consistently. Humans don’t. We trust familiar names. We want to be helpful. We don’t like delaying a request that feels urgent. And when something triggers fear or curiosity, logic often takes a back seat.
In the real world, this shows up in ways that feel ordinary:
- An email that looks like it’s from your manager asking for an urgent payment approval
- A phone call claiming to be IT support that needs your login details “right now”
- A text message warning you about a missed delivery or a locked bank account, pushing you to click before you think
The message itself isn’t always clever. What makes it work is timing, tone, and the very human instinct to respond quickly and move on with your day.
Fact: Social Engineering Implied in Majority of Reported Australian Cybercrime
Australia’s national cyber body logged over 84,700 cybercrime reports in 2024–25. Roughly one every six minutes.
Email compromise and business email fraud (both rooted in social engineering) were the most frequently reported types of incidents.

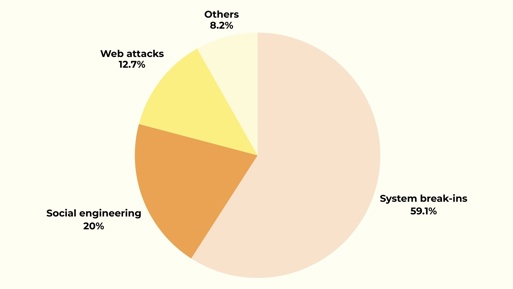
Common Types of Social Engineering Attacks
Social engineering comes in a few familiar forms. Once you know what they look like, you start spotting patterns everywhere. I’ll run through the most common ones and how they tend to show up in everyday situations.
1. Phishing and Spear Phishing
Phishing is the broad, mass-sent version. The same email goes to thousands of people, hoping a small number will bite. Spear phishing is far more targeted, and that’s why it’s so effective. I often point out that spear phishing emails are usually based on real details, like your role, your company, or recent activity. When a message feels personal and relevant, it’s much easier to trust it without questioning the source.
2. Vishing and Smishing
Vishing uses phone calls. Smishing uses SMS messages. Both rely heavily on urgency and authority. In Australia and New Zealand, these attacks often pose as banks, delivery companies, the Australian Taxation Office (ATO), or Inland Revenue (IRD). I’ve seen messages that look identical to legitimate bank alerts or parcel notifications. When a phone buzzes with a warning about money or missed deliveries, instinct kicks in fast.
3. Pretexting and Impersonation
Pretexting is about creating a believable story. The attacker pretends to be someone you already trust, like IT support, a supplier, or a senior colleague. I’ve seen cases where someone hands over access simply because the request sounds routine and professional.
4. Baiting and Quid Pro Quo
Baiting offers something tempting. Free downloads, dropped USB sticks, or “exclusive” access. Quid pro quo adds an exchange, like offering help or rewards in return for login details. Curiosity does the rest.

Why Social Engineering Is So Hard to Defend Against
This is the part I always come back to. You can lock down systems, update software, and deploy strong security tools, but you can’t patch human behaviour in the same way.
Technology follows rules. People don’t.
We get tired, distracted, rushed, or overly helpful, and attackers know exactly how to exploit that. It only takes a quick look at the top 5 cyber attacks globally over 2025 to realise how easy it is to fall for a trick that puts your organisation at risk, even if you work for a giant, household name company.
I often say that firewalls and antivirus software are essential, but they’re not designed to stop someone willingly handing over information. If a person clicks a link or shares access because they believe the request is genuine, most technical controls never even get a chance to step in.
That’s why awareness and training matter so much. I’ve seen well-protected organisations still fall victim because someone didn’t recognise the signs. The strongest defence isn’t just better tools. It’s people who feel confident pausing, questioning, and reporting something that doesn’t quite feel right.
Fact: Over Half of NZ Small Businesses Have Been Targeted by Scams
53% of New Zealand SMEs were hit by a cyber threat in the past six months.
This includes phishing and other scam activity: the kinds of social engineering tactics that exploit human trust rather than technical flaws. It highlights that businesses of all sizes face direct pressure from deceptive attacks.

How Organisations and Individuals Reduce the Risk
When talking about reducing social engineering risk, it always comes back to one thing: people's behaviour.
Policies and tools matter, but behaviour is what really changes outcomes. Awareness training works best when it’s practical, regular, and grounded in real scenarios, not just theory.
What organisations and individuals should focus on:
-
Building a security-aware culture where questioning unusual requests feels expected, not uncomfortable
-
Simple verification habits, like confirming payment requests or access changes through a second channel
-
Clear reporting processes, so people know exactly who to contact when something feels off
These small habits add up quickly.
Technology still has an important role to play. AI-driven tools can help by:
-
Spotting unusual behaviour patterns
-
Flagging suspicious messages earlier
-
Reducing the volume of obvious threats before they reach people
This works best as a support layer, not a replacement for human judgement. Our guide on the uses and impact of AI in cyber security breaks this down in more detail if you want to explore that side further.
Why Understanding Social Engineering Matters for a Cyber Career
From a career point of view, this is where social engineering really earns its place.
Employers aren’t just looking for people who know how tools work. They want professionals who understand how attacks actually play out in the real world, and why people are often the weak point.
Being able to recognise social engineering shows strong, practical cyber awareness. It signals that you can:
- think like an attacker,
- spot suspicious behaviour early,
- and understand the human context behind alerts.
That’s especially important in roles like Cyber Security Analyst or within Security Operations teams, where investigating unusual activity is part of the day job.
For career changers, this area often levels the playing field. Skills like communication, attention to detail, and questioning assumptions translate well into cyber roles. If you’re starting to explore a move into the field, it helps to understand the different routes people take when looking at how to get into cyber security.
To build this knowledge properly, many people choose structured training rather than self-teaching alone. Learning through recognised cyber security courses helps turn awareness of threats like social engineering into skills employers actually look for.
Key Takeaways: Explaining Social Engineering Simply
If you had to explain social engineering in one sentence, I’d put it like this: it’s about exploiting human behaviour, not breaking technology.
Attackers rely on trust, urgency, and routine to get people to make small mistakes that lead to big consequences.
Understanding this now helps you protect yourself and others, and it builds knowledge that stays relevant as threats evolve.
If you’re thinking about developing your skills further, speaking with one of our career experts can help you map out the next step. Booking a free consultation is often the easiest place to start.
Social Engineering FAQs
*This article was copy-edited by Adam Ashwell, a Senior Career Consultant in our Brisbane office, to adapt it for our readership in Australia and New Zealand. The original was written by Chris Ide, a Tech, IT, and Cyber Team Manager working in our UK headquarters.




