1. Marks & Spencer – a wake-up call for retail resilience
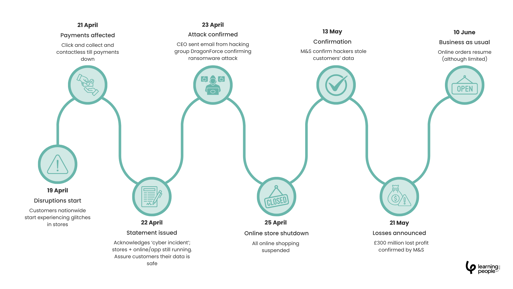
In April 2025, Marks & Spencer fell victim to a devastating ransomware attack by the Scattered Spider group. Using sophisticated social-engineering tactics, hackers infiltrated a third-party IT provider and encrypted company systems, stealing sensitive customer data in a double-extortion attack.
Within days, critical services, including click-and-collect, contactless payments and loyalty programmes, were offline. Analysts estimate the attack caused more than £60 million in immediate profit loss, wiped £1 billion from market value, and cost the retailer around £300 million overall.
The M&S breach highlighted the fragility of third-party systems and the urgent need for skilled professionals capable of detecting and responding to human-driven cyber threats.
2. Co-op – the ripple effect of social engineering
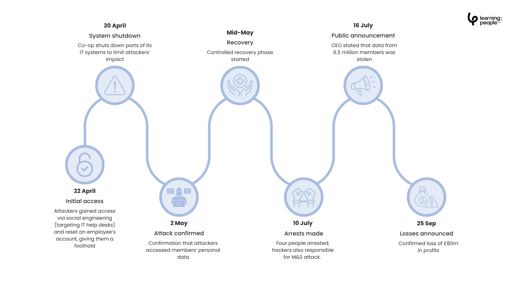
Just days after the M&S breach, the Co-op confirmed it too had been targeted by the same Scattered Spider group. The attackers used identical help-desk impersonation tactics to gain access, forcing Co-op to temporarily shut down parts of its IT systems.
While quick action prevented a full system compromise, the damage was already done. Data from 6.5 million members was stolen, and contactless payments were disrupted nationwide. The retailer reported an £80 million hit to operating profit and a £206 million revenue loss, pushing it into a pre-tax deficit.
From an open letter from Co-op for NCSC Annual Review 2025
“The buck stops with us as senior leaders. Please continue to consider the best route to protecting your business, but also the best means to defend against an attack, including supporting customers and colleagues, at every possible stage.”
3. Jaguar Land Rover – when manufacturing meets malware
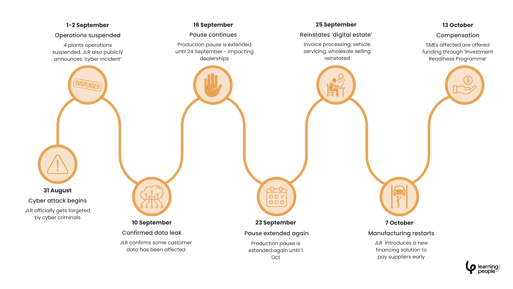
More recently, in August 2025, Jaguar Land Rover (JLR) suffered a crippling ransomware attack that brought its “smart factory” operations to a standstill. The damage of this attack is so monumental, experts at the Cyber Monitoring Centre (CMC) have estimated the event will cost an estimated £1.9bn and be the most economically damaging cyber event in UK history.
The Scattered LAPSUS$ Hunters group reportedly demanded payment after encrypting systems and exfiltrating data. The shutdown cost JLR an estimated £50 million per week, with wholesale sales down 24.2% and retail sales down 17.1% in Q2 FY26.
Production was suspended across multiple UK plants, halting deliveries and disrupting dealerships nationwide. Thousands of workers were impacted, and supply-chain partners needed emergency financial support.
The incident exposed the vulnerabilities of connected manufacturing systems and the need for cyber professionals who can safeguard operational technology as effectively as IT networks.
4. Qantas – a global lesson in vendor risk
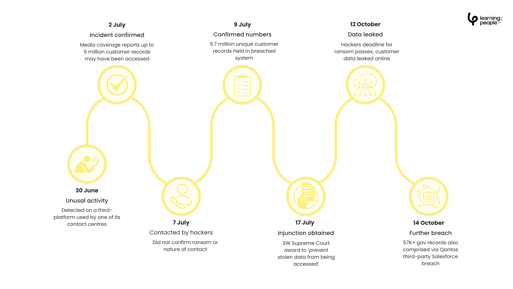
In July 2025, Australia’s flag carrier Qantas announced that hackers had accessed data from up to 6 million customers via a compromised third-party platform. The Scattered LAPSUS$ Hunters group exploited social-engineering tactics to infiltrate the airline’s systems, stealing customer information and demanding ransom.
While no credit card or passport details were stolen, the reputational fallout was huge. Qantas faced class-action threats and potential fines of up to $7 billion AUD, as well as a surge in customer complaints and inquiries.
This breach showed how supply-chain weaknesses can compromise even the most secure global enterprises, a clear call for improved vendor oversight and workforce cyber awareness.
In the age of AI, hackers don't break in, they're invited.
With every new technology development, they're getting better and better at asking to be let in.
When criminals posed as a Qantas IT contractor, they didn't need to crack encryption or breach firewalls - they simply asked. This pattern, which was repeated in recent attacks at M&S and Tesco, reveals an uncomfortable truth: the weakest link in cybersecurity isn't in the code, it's in us.
In the past 12 months social engineering tactics were involved in 98% of cyberattacks, and are now core to the playbooks used by criminal organisations. Pure technical hacks are rarer, and harder to pull off, so increasingly human beings are being targeted as the weak link.
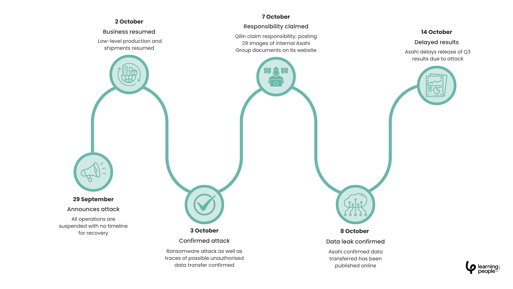
5. Asahi Group Holdings – disruption on an industrial scale
In September 2025, Asahi Group Holdings, one of Japan’s largest beverage manufacturers, experienced a crippling ransomware attack by the Qilin group. The assault forced the company to suspend production, shipments, and customer service across Asia-Pacific.
The Wall Street Journal estimated daily losses of ¥1.5 – 2 billion JPY (£7.4 – £9.8 million) during the shutdown. Data exfiltration further damaged trust with suppliers and retailers, as rival brands filled gaps on shelves.
The Asahi breach reinforced that ransomware is no longer just a data threat, it’s a strategic business continuity issue that can halt entire industries overnight.
Why cyber skills are now business-critical
2025’s wave of global cyber-attacks showed that even the most resilient and well-known brands can be brought to their knees by a single breach. Creating not only billions of lost revenue and complete halts to operations, these attacks also leave people out of work for months at a time. If these breaches highlight anything, it’s the growing need for highly skilled cyber security professionals.
Modern cyber security demands more than firewalls and software, it requires a human element from trained professionals who understand threat intelligence, risk management, and digital forensics to protect data, systems and people.
Sensitive corporate material and even guides on hacking are likely in the training sets of textual models like ChatGPT
Whilst these models are carefully moderated to guard against reproducing this verbatim, we have seen over the past year that they have proven vulnerable to creative workarounds and 'jailbreaking' techniques.
What this means for cybersecurity professionals in the future is that engineering solutions alone will not prevent these behaviours. The future of cybersecurity isn't just about building higher walls - it's about understanding the psychology of the people inside them. As AI continues to evolve, security professionals must become equal parts technologist, psychologist, and educator.
The constant shift and development of new techniques and programmes that threaten our data requires up to date and industry recognised qualifications. We can proudly say all of our pathways cover certifications from global leaders in cyber security including CompTIA, (ISC)² and EC-Council.
As part of our ongoing commitment to providing you with the highest quality training, we are the first and only training and careers company to work with the UK Cyber Security Council (UKCSC), the UK’s chartered body for cyber security. This means our CompTIA Security+ training is aligned with the UK’s highest professional standards in cyber security.
Now is the time to build the workforce that keeps our digital world safe, one skilled professional at a time. Join the future of cyber security by arranging a free call now.
Related Articles
 Cyber Security
Cyber SecurityReflecting on the top 5 global cyber-attacks of 2025 – the growing need for skilled cyber professionals
We take the time to reflect on some of the most news-worthy cyber-attacks, how they happened, and what it says about the global cyber skills gap.
Read More Cyber Security
Cyber SecurityLearning People's Security+ Training is Now Recognised by the UK Cyber Security Council
As a trusted and globally-recognised provider of Cyber Security training, we are delighted to announce that our Security+ course syllabus is now fully mapped to the Associate level of the UKCSC’s Standard of Professional Competency & Commitment.
Read More Cyber Security
Cyber Security49% of UK businesses have a cyber security skills gap, according to Gov report
The UK is in dire need of certified cyber security professionals to protect businesses according to the UK Government
Read More AI
AIHow AI is shaping the future of cyber security
Learn the importance of data visualisations when telling compelling data stories, along with the common pitfalls faced by Business Analysts and Data Analysts.
Read More

